
ABISHEK LAKANDRI
Dive into a world of cybersecurity insights, IT tutorials, and step-by-step guides on a variety of tech topics. This blog is not only a place where I share my journey and learning experiences in the field of IT and cybersecurity, but also a resource to help you overcome challenges you might face along the way.
-
How to Install and Use Metagoofil on Kali Linux
How to Install and Use Metagoofil on Kali Linux Metagoofil is a powerful OSINT (Open Source Intelligence) tool used to search Google for specific file types hosted on a…

-
Step-by-Step Guide: Enabling SSH on Ubuntu
Step-by-Step Guide: Enabling SSH on Ubuntu This guide will walk you through the process of enabling SSH on an Ubuntu system. Follow each step carefully to ensure SSH is…
-
Privilege escalation on Linux: When it’s good and when it’s a disaster (with examples)
For authorized users on Linux, privilege escalation allows elevated access to complete a specific task or make system configuration modifications. For example, system administrators may need access to troubleshoot…
-
Linux chmod and chown – How to Change File Permissions and Ownership in Linux
Linux is a multi user OS which means that it supports multiple users at a time. As many people can access the system simultaneously and some resources are shared,…
-
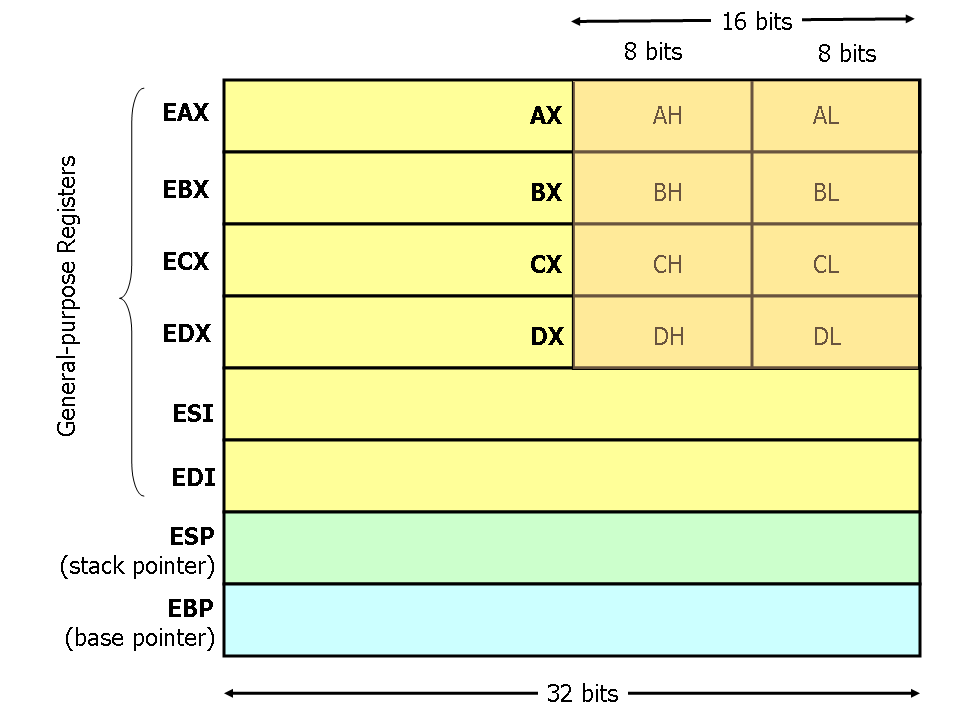
Understanding Key CPU Registers in x86 Architecture
Hi Guys, Here I am back with another article about “CPU REGISTER”. I will be telling you the most Important Registers Used by Hackers to Compromise the System or Memory Based…
-
How to SSH into HostGator cPanel: Step-by-Step Guide
Learn how to securely SSH into your HostGator cPanel with this easy step-by-step guide, including generating SSH keys, setting permissions, and connecting from your terminal. Introduction:If you’re managing your…

