Hi Guys, Here I am back with another article about “CPU REGISTER”. I will be telling you the most Important Registers Used by Hackers to Compromise the System or Memory Based Exploits. you have to research a lot for this I will just give you a better understanding of CPU Registers.
What is a Register ?
•Think of this as a variable special to the CPU
•The CPU only has a set number of registers
- Each have their own use and function for the CPU to use
Register are used to quickly accept, store, and transfer data and instructions that are being used immediately by the CPU, there are various types of Registers those are used for various purpose.
Types Of CPU Registers looked by Hackers are :
•EAX
•EBX
•ECX
•EDX
•ESI
•EDI
•EBP
•ESP
- EIP
About EAX (Extended Accumulator Register)Register
•EAX is most commonly used as the return value of a function
•When an application does something like:
•Return True
•The value of True will be in EAX at that time
- This is also considered a special purpose register for things like multiplication and division.
About EBX(Extended Base Register)
•EBX has no special purpose specifically
•This is most commonly used to help hold a value while performing calculations of some kind
- This will commonly hold the value of 0 for quick access to that value.
About ECX and EDX
ECX
•ECX is also known as the counting register
•When you perform a loop this will often be the iterator that is used
•Can be used to count up to a digit or own to 0
EDX
•EDX is commonly used to hold parameters passed by functions
- Can also be used to hold temporary data
About ESI and EDI
ESI
•This is often used as a pointer
•Normally points to the source of the data so it can be referenced without changing it
EDI
- Similar to ESI EDI will generally point to the destination for data
About EBP Register
•EBP can be used for temporary storage
•This is also used commonly with compilers
•This will keep track of the stack pointer when a compiled application is not set to optimized
- When it is set to optimized it will not be used for any compilation of an application
About ESP Register (Imp)
•ESP is a special purpose register
•This points to the top of the stack
•ESP is not normally changed unless required to do so
•Is not normally used for temporary storage
- When manipulating a binary to create your own backdoors keeping this value will be important
About EIP Register (Most Imp For Hackers !)
•EIP is one of the most single important registers you can use
•Is is also called the instruction pointer
•Whatever is in this register is what will be executed next
•This is commonly the target of memory based exploits
- Controlling this register often means a compromise of the system
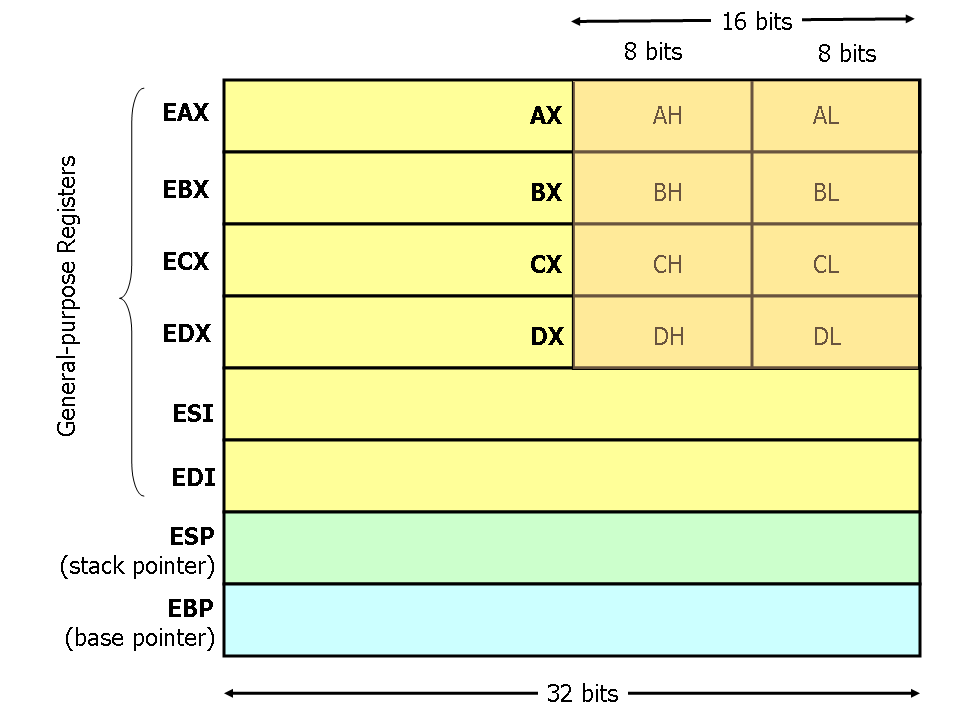
High & Low Registers
•Each register is 32 bits
•There are 3 sub versions of each register
•Using EAX as an example
•EAX: Can hold the full 32 bit value
•AX: only handled the last 16 bits of the 32
•AL: Handles the lower 8 bits of the 32
•AH: handles the bits 8–15 of the 32
•It is important to understand that there are these sub versions of registers as you may not want to use up the full 32 bits for something that is 5 bits
- The sub registers are also used for multiplication, division, etc.
Thanks For Precious Time for reading this article !! Thanks to Read Team Nation

Leave a Reply